General
Authentication
How often is a device typically authenticating against RADIUSaaS?
This is difficult to answer as it depends on the behavior of your users, clients, and networking gear (APs, NACs, switches). Additionally, it is important to note that RADIUSaaS will neither
trigger an authentication nor
send a termination request via its accounting port to the client, potentially triggering a re-authentication.
If you feel your devices are authenticating very frequently (multiple times an hour) without the user constantly restarting the client, then this could be for the following reasons:
The network controller doesn't authenticate the client fast enough for the client to join the network, so the client attempts to authenticate again. Check the network controller to see if/when it is receiving an answer from RaaS.
The network controller is re-initiating authentication. Check the network controller for what might be causing this.
RADIUSaaS Admin Portal
How can I add the RADIUSaaS Admin Portal to My Apps?
Create the App
First, you have to create an Enterprise app. To do this via the Azure portal, follow these steps:
Login to your Azure account
Go to Microsoft Entra ID
Select Enterprise applications
Click + New Application

Click + Create your own application
Give a name for the app (e.g. RADIUSaaS Portal)
Choose Integrate any other application you don’t find in the gallery and
Click Create

After that the app is set up, we now need to add users to it and configure the logo and link
Add Users and a Logo
Under Manage go to User and groups - Add all users/groups who should be able to view/use your new URL tile and save
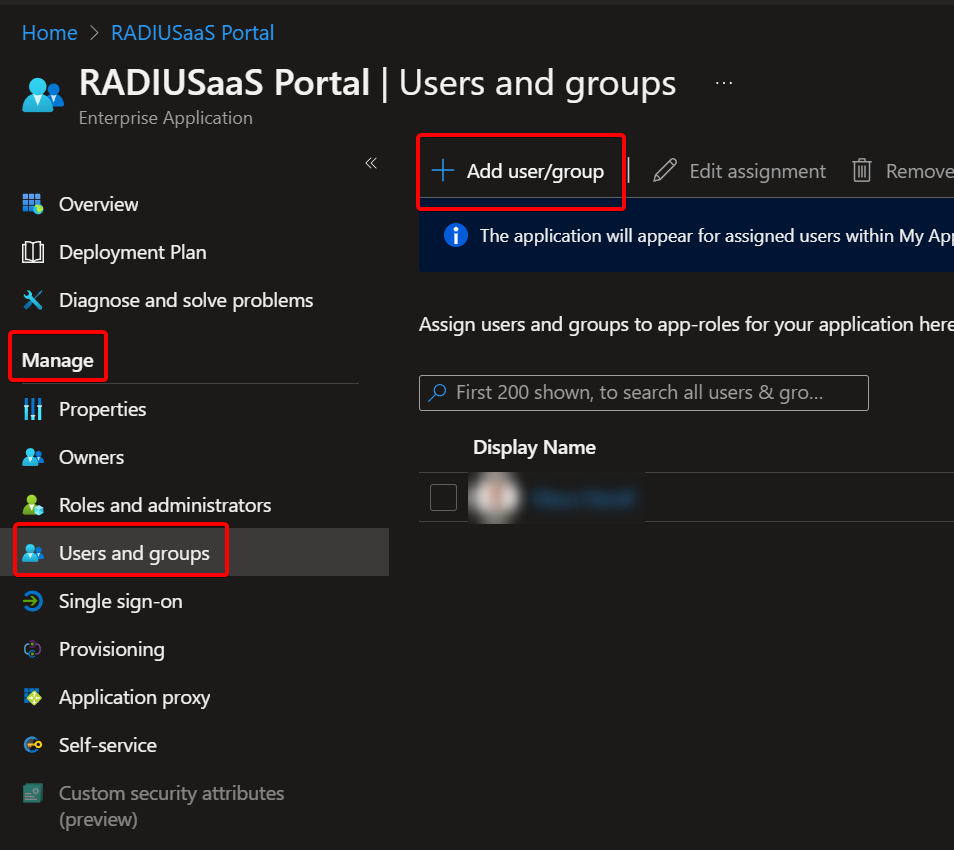
Click "User and groups" Click Properties - Upload an image logo of your choice and save
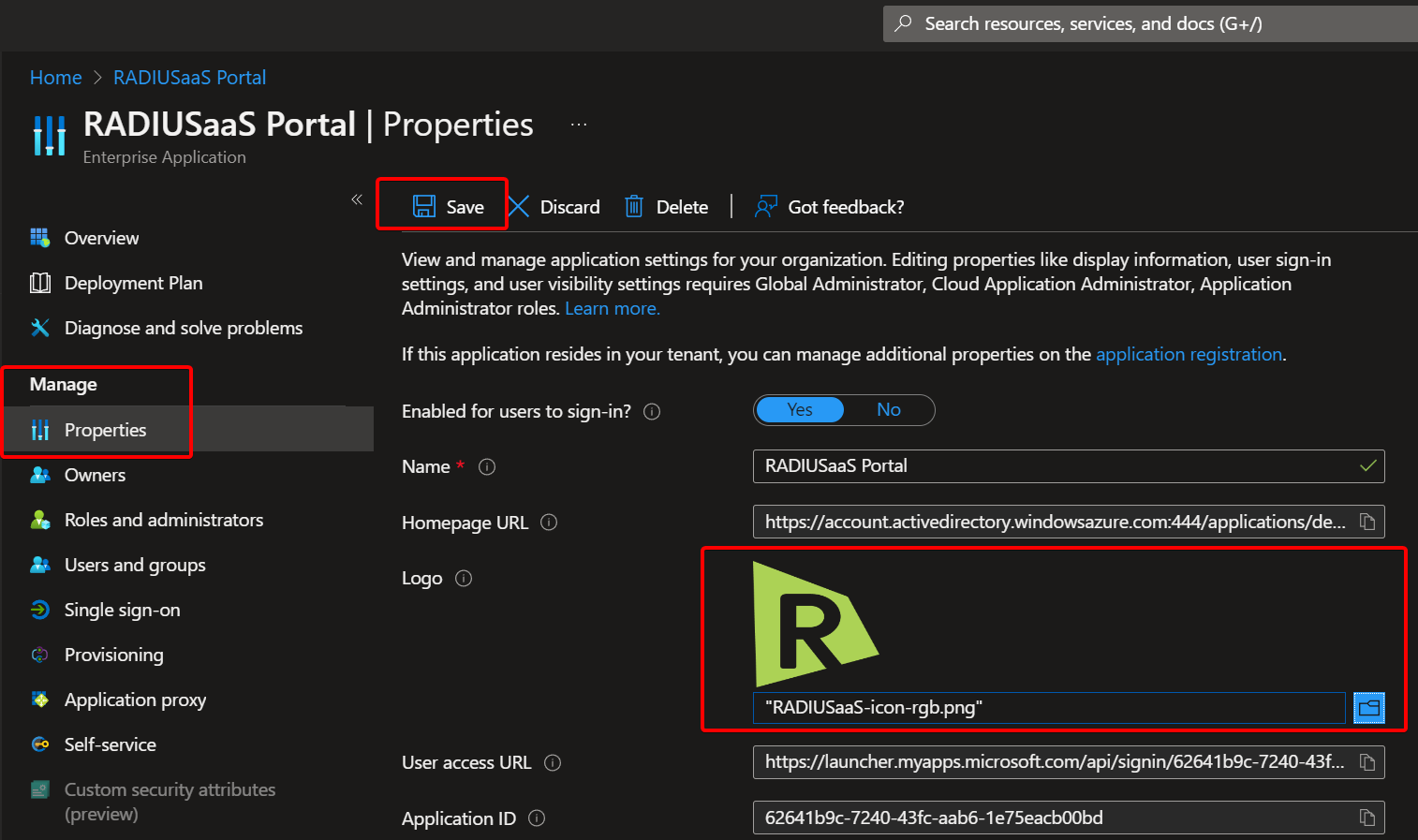
Click "Properties" Click Single Sign-on - Select Linked mode - Then enter the URL you want and save.
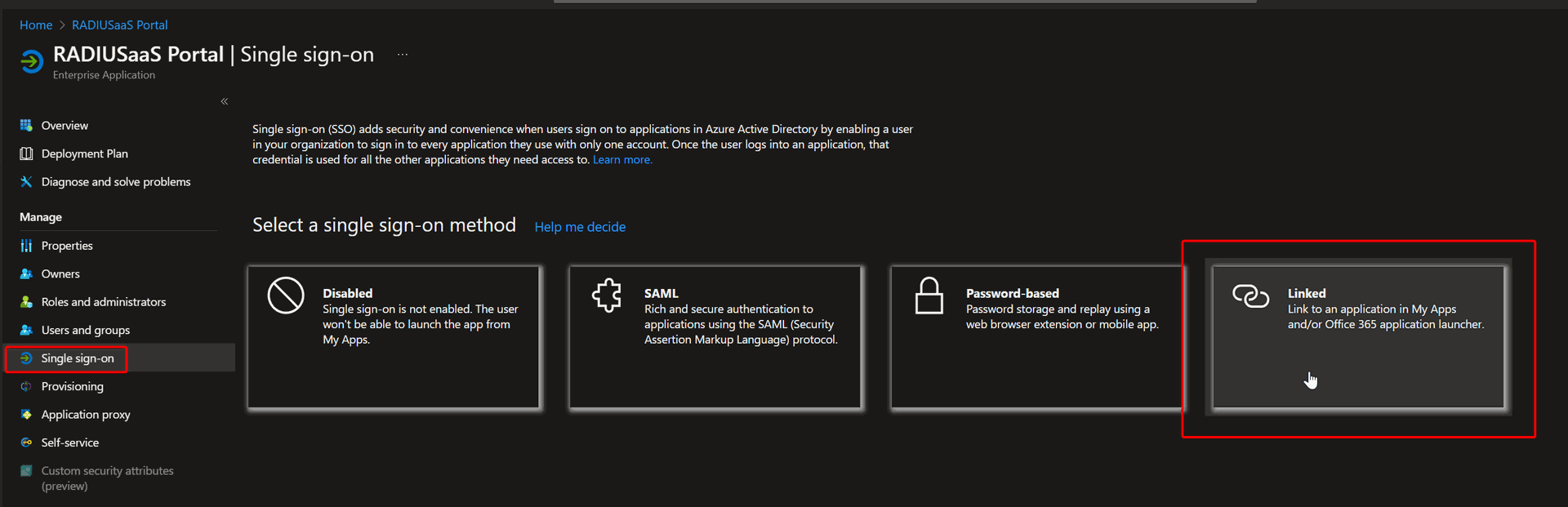
Click Single Sign-on - Select "Linked" mode

Access My Apps
Your users should now be able to access the newly created link tile via My Apps.
RADIUS Return Attributes
Which VLAN-related attributes does RADIUSaaS return by default?
In case you require other VLAN attributes than returned by default, please contact our support.
If VLAN tagging is enabled by configuring and enabling a relevant Rule, RADIUSaaS returns the following generic VLAN attributes
"Tunnel-Type": "VLAN"
"Tunnel-Medium-Type": "802"
"Tunnel-Private-Group-ID"
along with the other commonly used vendor-specific VLAN attributes:
"WiMAX-VLAN-ID"
"Nexans-Port-Default-VLAN-ID"
"Dlink-VLAN-ID"
"UTStarcom-VLAN-ID"
"DHCP-IEEE-802.1Q-VLAN-ID"
"Motorola-WiMAX-VLAN-ID"
"Telrad-C-VLAN-ID"
"Telrad-S-VLAN-ID"
"SN-Assigned-VLAN-ID"
"Extreme-VM-VLAN-ID"
"Ruckus-VLAN-ID"
"Mikrotik-Wireless-VLANID"
"Egress-VLANID"
"HP-Egress-VLANID"
Secondary Instance and Failover
How does a secondary instance behave in terms of failover?
A secondary instance means that you have at least a secondary RadSec server that works independently of your main instance but has the same configuration. If you have one, you can see multiple IP Addresses under RadSec IP Addresses.
RadSec Connection
Since the RadSec servers are independent of each other, they will not handle any kind of failover. You should add both IP addresses/DNS entries to your Network controller which decides to which server the authentication requests are forwarded.
RADIUS Connection
With your RADIUS proxies, it's a little different: Your proxies are aware of each of your RadSec instances and their health states and thus will handle failover if the primary server fails.
Timers & Timeouts
What EAP parameters and timeouts should be configured?
Not every access point or switch (authenticator) provides you with the same amount of configuration options for EAP and general (RADIUS server) timeout parameters. Below overview presents the maximum set of parameters known to us and how they should be configured to allow for maximum reliability of the connection between the authenticator and RADIUSaaS.
RADIUS Server Timeout
5 seconds
EAP Parameters
EAP timeout
15 s
EAP max retries
5
EAP identity timeout
10 s
EAP identity retries
5
EAPOL key timeout
2000 ms
EAPOL key retries
4
Logs
How can I identify the public IP address of the site from which an authentication originates?
To identify the public IP of the authenticating site for a particular authentication, the approach depends on whether you are using a RADIUS connection (via the RADIUS proxies) or a direct RadSec connection:
RadSec Connection
Navigate to Insights > Logs.
Configure the relevant timerange / search window.
Set the Logtype filter to details.
Identify the relevant authentication (by correlating the timestamp and username).
Identify an
Access-Requestmessage (message > Packet-Type = Acess-Request) that belongs to the authentication under investigation.Expand the respective log entry.
The public IP can be extracted from the message > Packet-Src-IP-Address property of the log entry.

RADIUS Connection
Navigate to Insights > Logs.
Configure the relevant time range / search window.
Set the Log-type filter to the proxy.
Identify the relevant authentication (by correlating the timestamp and username).
The public IP can be extracted from the message property of the log entry:

Does RADIUSaaS support WPA3 Enterprise?
Yes, RADIUSaaS supports WPA3 Enterprise. It also supports WPA3 Enterprise 192-bit mode with the following limitation:
Windows 11 24H2 introduced stricter certificate requirements for WPA3-Enterprise 192-bit encryption, leading to authentication failures if the entire certificate chain does not meet specific cryptographic strength standards. This update mandates RSA key lengths of at least 3072-bits or ECDSA with the P-384 curve for all certificates involved in the authentication process. Organizations using certificates with weaker parameters, such as RSA 2048-bit, may encounter issues.
While SCEPman supports 4096-bit RSA keys for Windows, this is limited to the Software Key Storage Provider (KSP), as the hardware TPM does not support this key size.
If after upgrading to Windows 11 24H2 you experience authentication issues, look for "SEC_E_ALGORITHM_MISMATCH" errors in the Event Viewer (System Logs and CAPI2) as an indicator for incompatibility in the cryptographic algorithms between the client and the server.
What can I do if I want to use WPA3-Enterprise authentication on Windows?
Your current option moving forward is to address the certificate requirements for WPA3-Enterprise 192-bit on your Windows 11 24H2 clients. This includes updating the Leaf Certificate to meet the new minimum requirements.
Please note that Intune does not currently include an option in its SCEP profile to specify a key size of 3072-bits which could be stored in the Trusted Platform Module (TPM) of the receiving computer. Due to this limitation, currently the only feasible solution for Windows clients is to use 4096-bit RSA key enrolled in Software Key Storage Provider (KSP).
As Intune's WiFi profile only provides WPA2-Enterprise you will need to use an external tool to create a WPA3-Enterprise WiFi profile. For convenience, RADIUSaaS includes this tool here.
Last updated
Was this helpful?