Security & Privacy
This chapter provides an overview on frequently asked questions surrounding information security, privacy and quality assurance.
Data Processing and Permissions
1. From what data center is RADIUSaaS operating?
Continent
Region
2. Which data is processed by RADIUSaaS?
Certificates
RADIUS Protocol
Miscellaneous
3. Which data is persistently stored by/on behalf of RADIUSaaS and how?
4. Is there an archiving mechanism for logs?
5. Which tenant permissions do users accessing the RADIUSaaS web portal have to consent to?
6. What data is made available by granting the consent(s) from 5.?
7. Which externally accessible endpoints does RADIUSaaS expose?
8. How are the endpoints from Question 7 protected?
9. What ports and protocols are used by the endpoints from Question 7?
Identity
1. What authorization schemes are used to gain access to RADIUSaaS?
2. Are there conditional access / role-based access controls in place to protect RADIUSaaS?
3. Can access credentials be recovered? If yes, how?
Data Protection
1. How is data at-rest protected against unauthorized access?
Configuration Data and Secrets
Kubernetes Service
Logs
2. How is data in transit protected against unauthorized access?
3. How are customer tenants separated from each other?
Backend
RADIUS proxies
Security by Design
1. Does RADIUSaaS employ a defense in depth strategy?
2. Is the UDP-based RADIUS protocol secure?
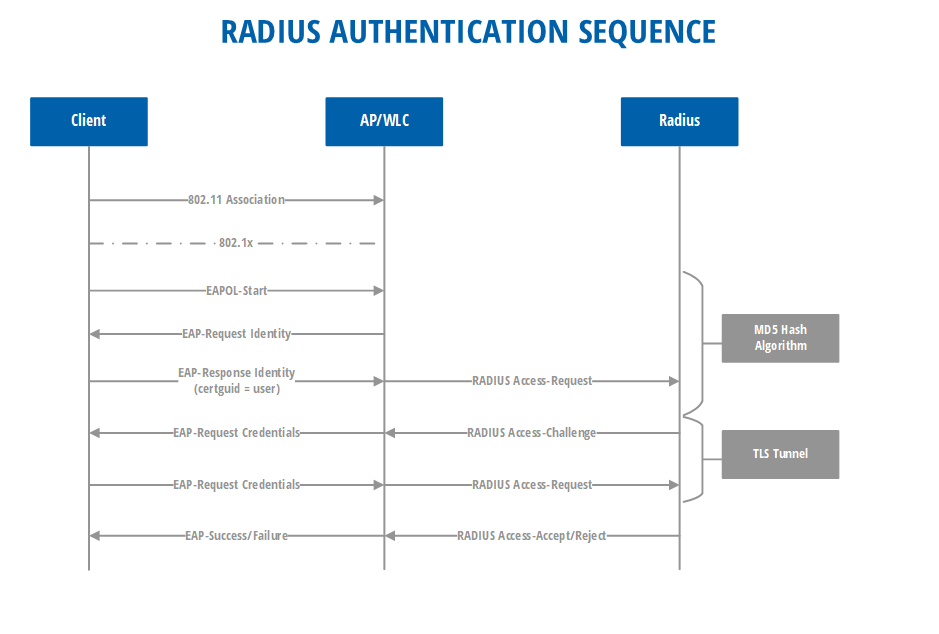
3. What technologies, stacks, platforms were used to design RADIUSaaS?
GDPR and Data-residency
1. Is data leaving Europe?
2. What 3rd-Party cloud-providers does RADIUSaaS rely on and why?
Company
Services
Contact
Purpose
Miscellaneous
1. Is RADIUSaaS part of a bug-bounty program?
2. What QA measures are in place?
3. Do you regularly perform penetration tests?
4. Is there a patching process in place?
5. What are the SLAs for patches?
6. Does RADIUSaaS perform backups?
Secrets and configuration data
RADIUS and RadSec servers
Logs
7. Are there backup restore tests?
Last updated
Was this helpful?