Juniper Mist
Prepare certificates
To establish a valid RadSec connection, your Access Points must trust the RADIUS Server Certificate and your RADIUS server must trust your RadSec Client Certificate. To achieve this,
Download the root certificate of the CA that has issued your active RADIUS Server Certificate as described here.
Create a RadSec Client Certificate for your Access Points. If you are using SCEPman Certificate Master, the process is described here.
Ensure to monitor the expiry of your RadSec Client Certificate and renew it in due time to prevent service interruptions.
Add the root certificate of the CA that has issued the RadSec Client Certificate to your RADIUS instance as described here and select RadSec under Use for. In case the RadSec Client Certificate has been issued by SCEPman and you already trust the SCEPman Root CA for client authentication, simply edit the trusted SCEPman Root CA certificate and select Both under Use for.
Mist configuration
Below settings are the necessary settings to establish a functional RadSec connection with our service. Configure any other settings at your discretion.
Navigate to your Mist configuration plane.
To configure the relevant certificates, navigate to Organization > Settings.
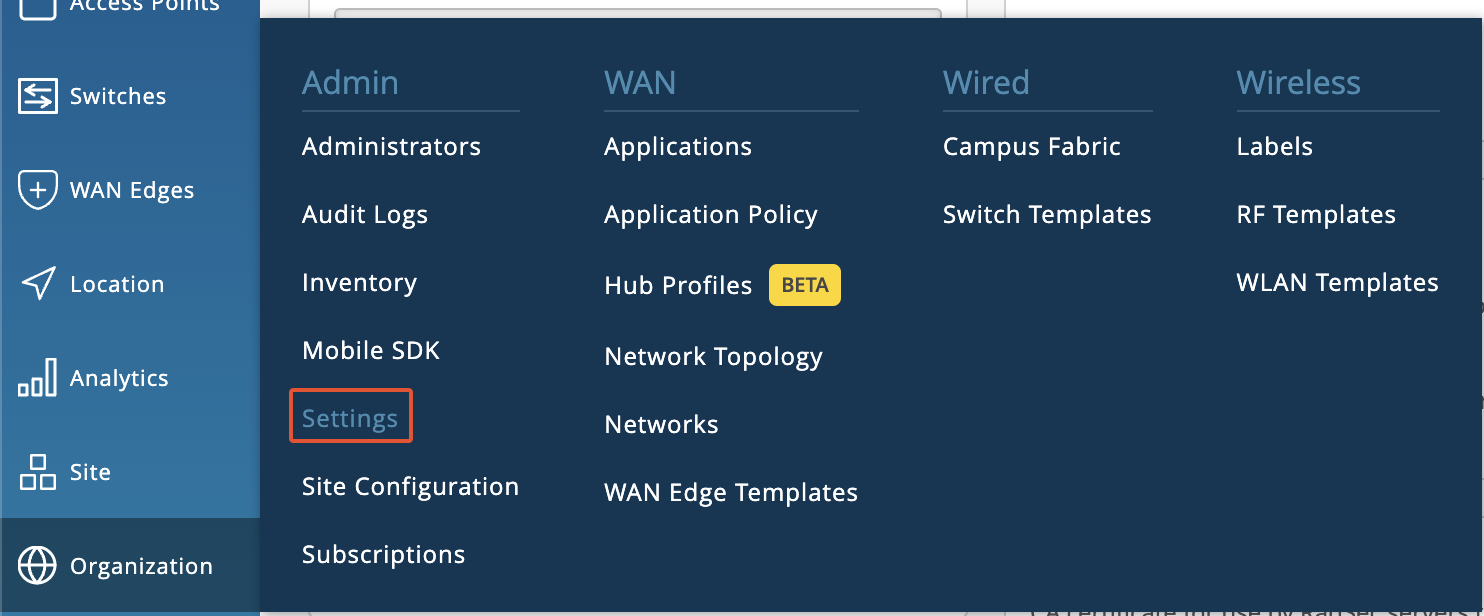
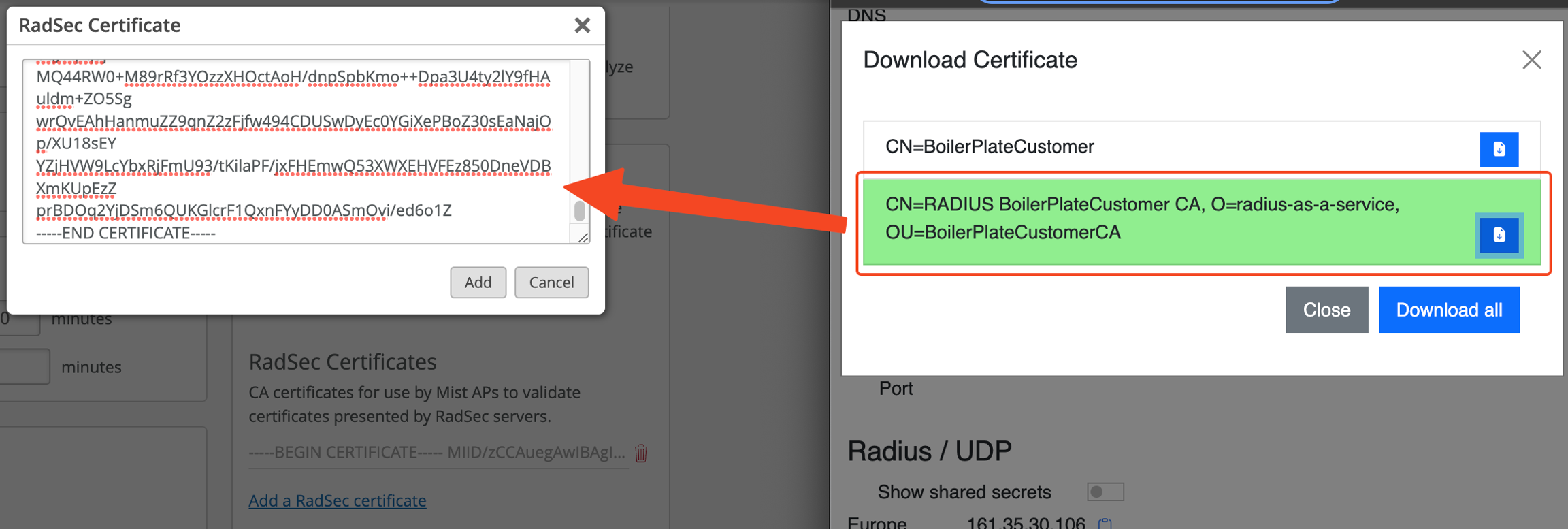
Add the root certificate of the CA that has issued your RADIUS Server Certificate under RadSec Certificate.
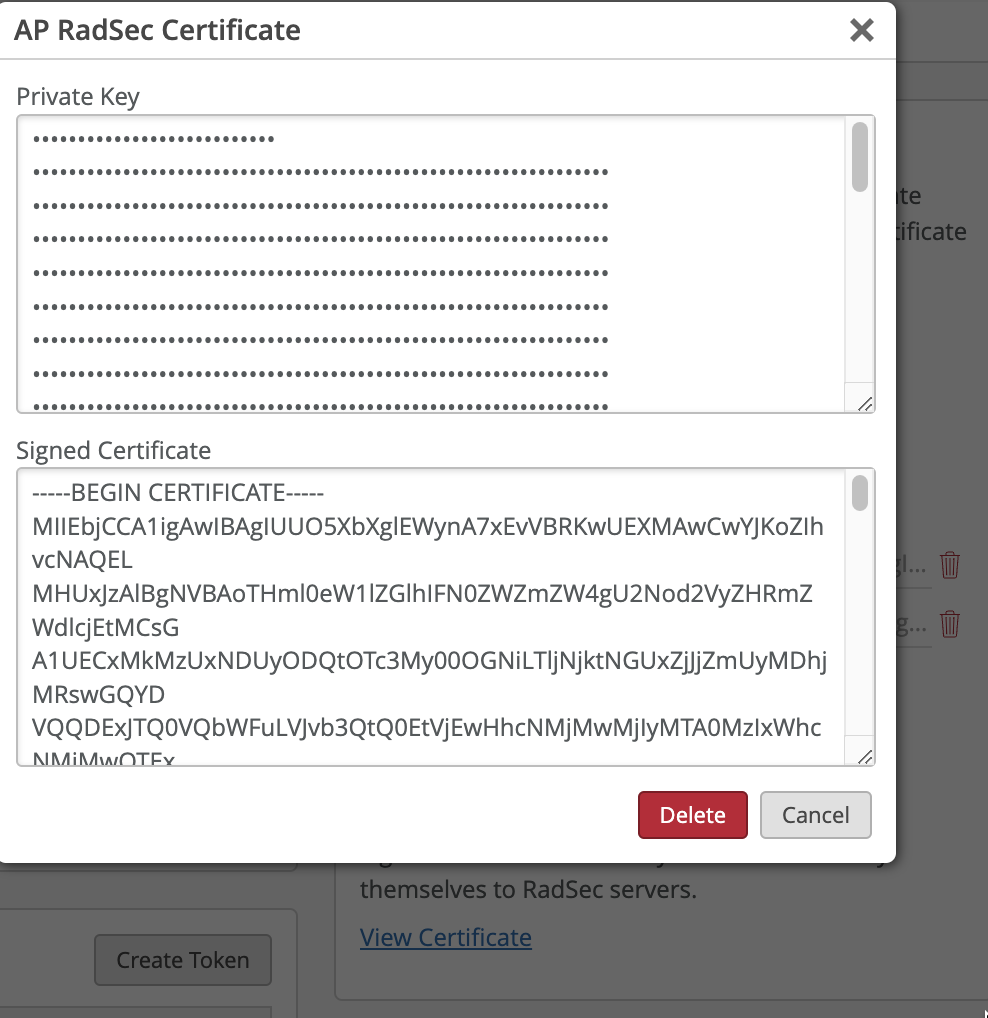
Add your RadSec Client Certificate (created in step 2 under Prepare Certificates) to AP RadSec Certificate.
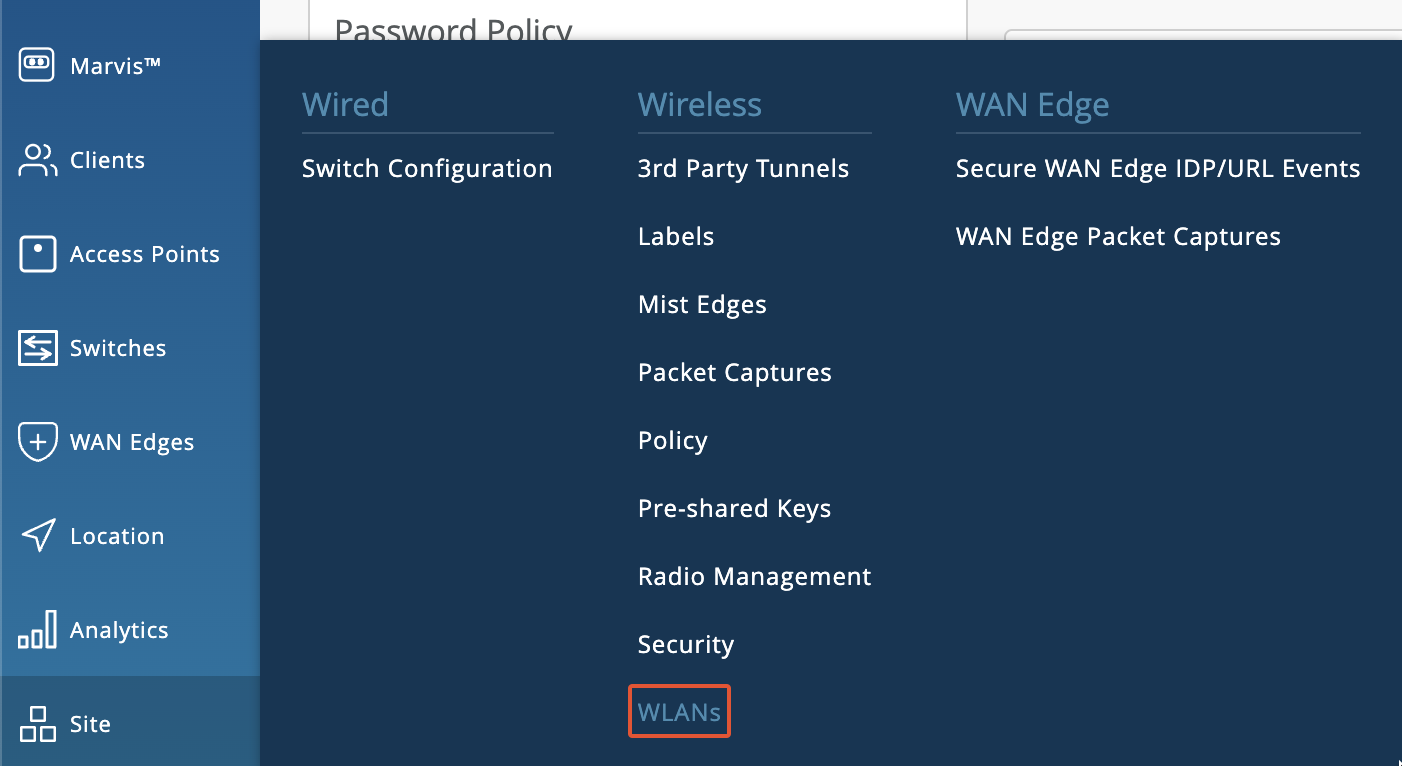
Go to Site > WLANs.
Create a new WLAN if you have not already created one for which you want to leverage RADIUS authentication against our service.
Select Enterprise (802.1X) as Security Type.
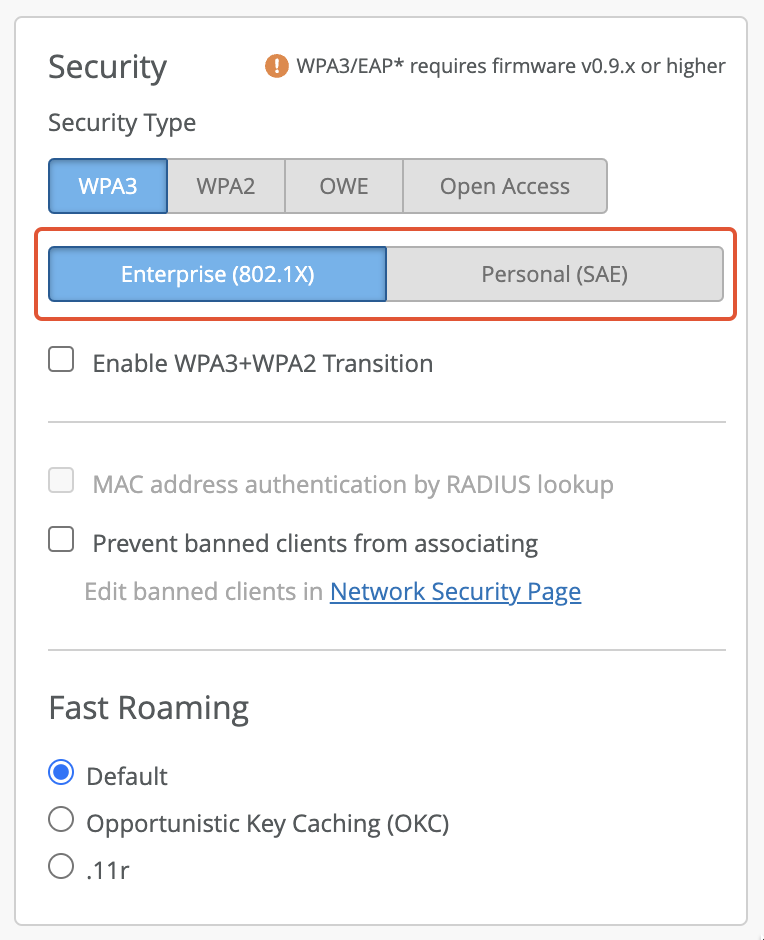
Under RadSec, select Enabled and set the Server Name to the SAN attribute of your RADIUS Server Certificate.
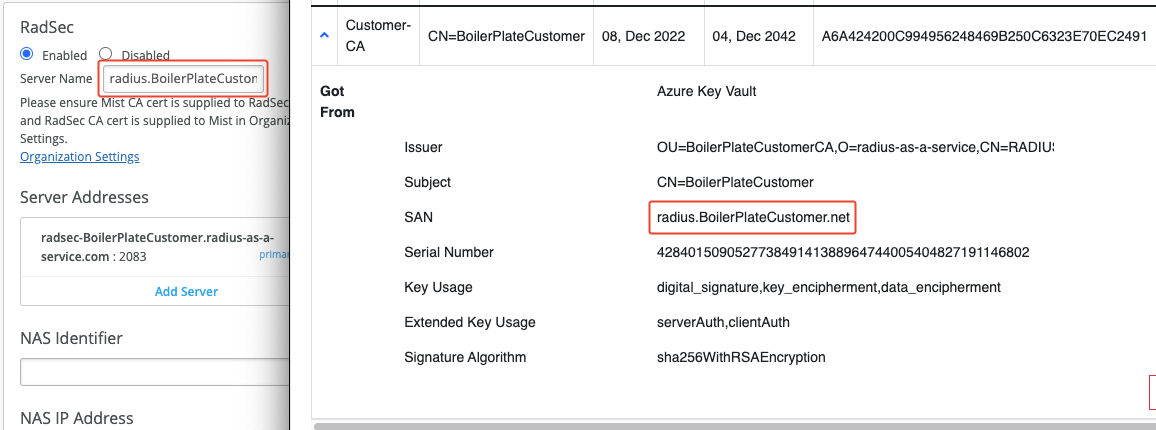
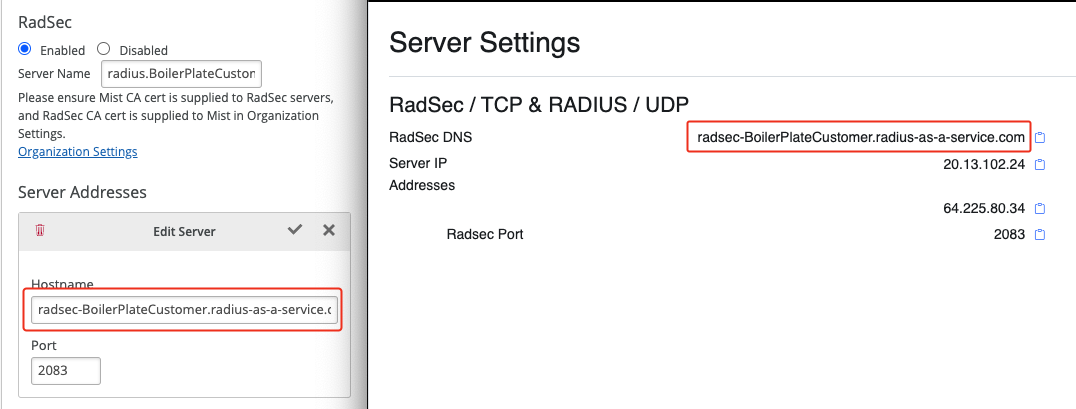
For Server Addresses use either the IP address or the DNS name of your RadSec service endpoint.
A complete walk-through

Last updated
Was this helpful?